How to get vCenter updates through a proxy using the Appliance MUI (or VAMI)
In yesterday’s post, I updated my VCSA 6.0 appliance to version 6.5. Today, logged into the Appliance MUI and noticed that my appliance was not able to check for updates using the default web repository.
Before we really start, a quick note on terminology. The Appliance MUI (which means Appliance Management UI) is the new name for the old VAMI (vSphere Appliance Management Interface). The MUI is a HTML5 web interface for configuring basic and low-level settings for the VCSA. It’s accessible by connecting to your VCSA on port 5480.
So, what’s the deal? Well, when browsing to the update section of the MUI and checking for updates, I would receive the following error:
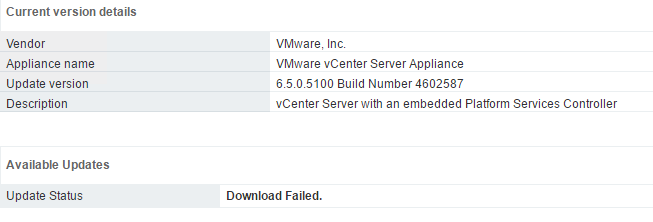
My proxy config was the first thing I checked. You can check the proxy in the MUI under Networking > Manage > Proxy settings. Sure enough, my config was correct for my environment.
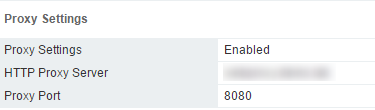
I also knew that my proxy was working correctly and was contactable by my VCSA, because I was able to use the proxy for the VCSA 6.5’s integrated update manager to communicate with the default web-based patch repositories.
I did a web search and came across an awesome post which contained the solution, written by a vExpert named Mario. Full credit to him - the solution to this problem is his and not mine. I encourage you to check out his blog.
So, it turns out that when you configure a proxy via the MUI, it only configures the proxy as a HTTP proxy. As Mario points out (as does the GUI in the screenshot above - if you’re paying attention), the update repository is a HTTPS address, so the proxy configured via the MUI won’t apply. Why doesn’t the proxy you configure apply to both HTTP and HTTPS connections, I hear you ask? I haven’t got a clue.
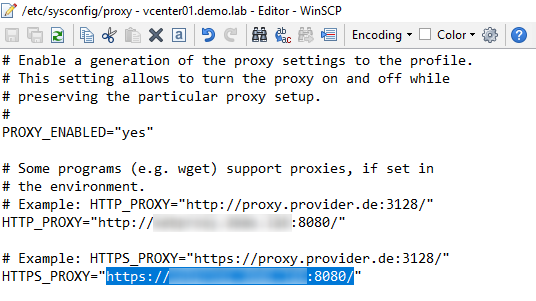
The solution is surprisingly simple, once you’ve got some instructions and know where to look (which I didn’t). Simply edit the /etc/sysconfig/proxy file via SSH or WinSCP (which is the option I took), and manually configure the HTTPS proxy - taking care, obviously, to adjust the URL from HTTP to HTTPS (highlighted).
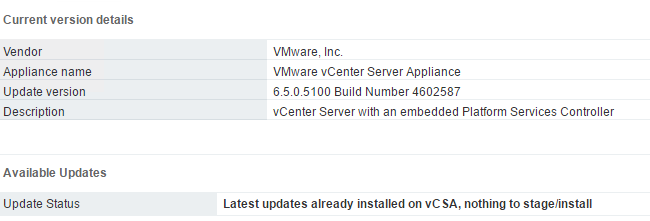
After saving the changes, return to the updates section of the MUI and try checking for updates again. Boom! Thanks, Mario!
Edit: As of the 23rd October 2017, I’ve been notified in a comment below by Stijn that a bug exists with vSAN 6.6 as documented in KB 2150523 where the configuration of any proxy, even through the GUI, will break the vSAN management service. I would suggest unconfiguring the proxy on all of your vCenter Servers which are managing vSAN 6.6 clusters until this bug is resolved. Thanks Stijn for pointing this out!
comments powered by Disqus